For those responsible for the cybersecurity of critical networks, a “threat profile” (TP) is an extremely valuable tool. A TP identifies and documents potential vulnerabilities (or “findings”) related to an assessed piece of software. Using a TP, experts can better prioritize, develop and deploy effective approaches to mitigate the identified vulnerabilities. TPs also communicate risk to users by documenting all that has been done to boost cybersecurity. ACE IoT Solutions is pleased to spread the word that the Pacific Northwest National Lab (PNNL) has released a Threat Profile for VOLTTRON, the open source energy data and DERMS platform.
Why should the VOLTTRON user community - and proponents of open source technologies - cheer PNNL’s development and publication of these documents?
First and foremost, the TP and related documents provide evidence of the security of the VOLTTRON Platform. While nobody can promise complete security for any system, the due diligence PNNL’s Secure Software Central (SSC) employed for VOLTTRON shows the extent to which the VOLTTRON team goes to secure its software. A second reason to cheer the release is that the reports demonstrate the Department of Energy (DoE) and PNNL’s ongoing commitment to VOLTTRON. The reports and the energy and resources behind the assessments should provide current and potential users of VOLTTRON with confidence in the tool. A final reason to cheer is that the reports illustrate a distinctive attribute of open source systems when it comes to assessing and mitigating cybersecurity threats. When ACE IoT Solutions interviewed Chance Younkin, a Cyber Security Engineer at PNNL, he made this very point.
“The highly collaborative approach between the VOLTTRON community and the team was hugely beneficial to the threat assessment process. Users in the VOLTTRON community can independently verify the Threat Profile and the efficacy of potential risk mitigation. Threat Profiles can be easily customized for different users, providing specific controls for each use case. But the Open Source nature of VOLTTRON allows that knowledge to be shared back to the community, which leads to increased security throughout. Of course, this is most often not the case with proprietary systems, where users have no choice but to trust that a vendor’s software developers are being vigilant and transparent when it comes to mitigating cyber threats. This kind of collaboration is only possible because VOLTTRON is open source”
Chance Youkin, PNNL
Summaries of the PNNL Releases
Last week, PNNL’s Secure Software Central (SSC), a capability that strives to bring cybersecurity to all aspects of the software development life cycle, released three documents pertaining to cybersecurity and the VOLTTRON™ Platform.
- The VOLTTRON Threat Profile is an assessment that provides mitigations and controls against specific threats to VOLTTRON. The TP is the centerpiece and final outcome of SSC’s Threat Based Software Analysis. The TP focuses on the cybersecurity of the software with emphasis on the deployed environment. Using standards such as Microsoft’s STRIDE model and the CIA triad, the TP maps actionable controls directly to attack paths, which map directly to diagrams of the system and the assets that need protection. Red entries in the text are controls that will be implemented in VOLTTRON 7.0. Others were already in place, but the Threat Profile lists them as well for awareness and justification purposes.
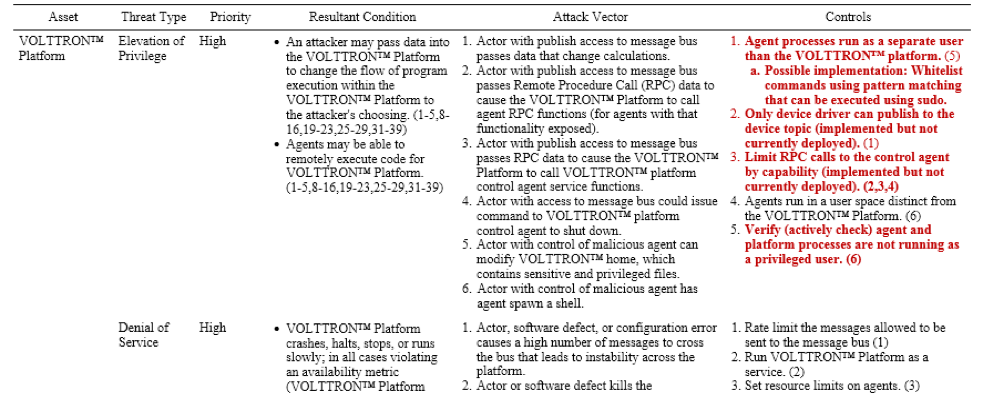
Table 1. Snippet of Threat Profile for VOLTTRON PNNL Campus Deployment
TPs bring value regardless of the development stage of the software. They yield actionable controls for mature software, they establish security requirements when no code is written, they provide justification for taking security measures because the controls show exactly what can be compromised.
- The Community Security Report lays out representative commercial use cases for which Threat Profiles can be developed. The CSR lays out the need for the community to get involved in secure software development practices. In this report, SSC engaged with representatives from the VOLTTRON community to develop two use cases that generally cover most VOLTTRON deployments. Initial Threat Findings (the second stage of the 3-stage process of developing Threat Profiles) were described to showcase the potential for bolstering cybersecurity in various VOLTTRON environments. This diagram will drive the Threat Based Software Analysis leading to the Threat Profile for Flat Topology.
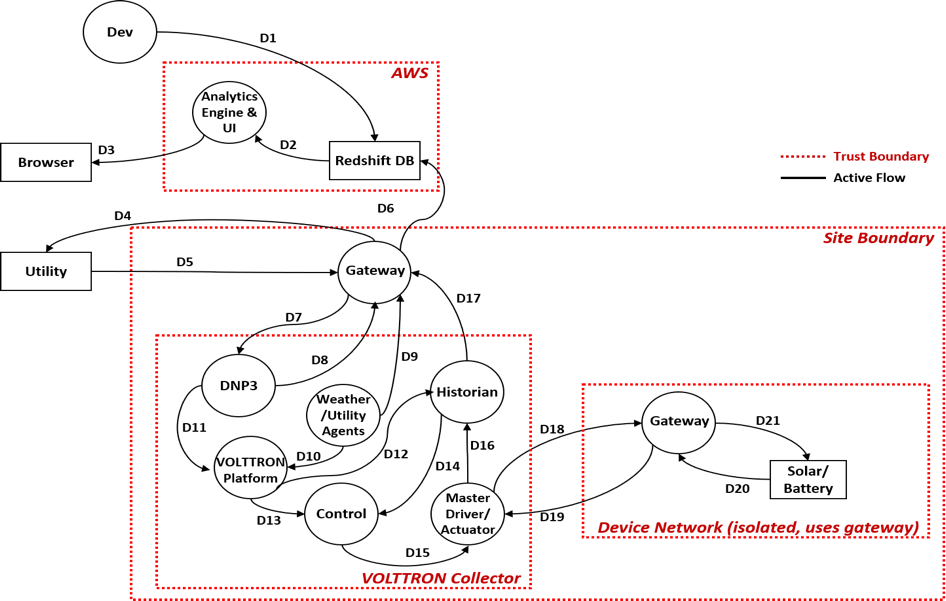 Data Flow Diagram for the Flat Topology Use Case
Data Flow Diagram for the Flat Topology Use Case
The CSR also provides guidance for further VOLTTRON development with several focus areas. From security logs for forensics analysis to web resources, to cloud, these preliminary findings are only the start of a more complete threat profile offering.
- SSC - The VOLTTRON Case describes the strategy and processes employed in developing Threat Profiles for VOLTTRON use cases. This is the “process report” that describes in some detail just how the Secure Software Central team operates. The theme is one of offering value at every step and doing it regardless of development stage of a software project. The report lays out the ideal cycle of doing Threat Based Software Analysis followed by Secure Software Development but emphasizes that this cycle is by no means necessary. In the “startup” stage, SSC will meet a project where they are, determine what is needed and how, and then focus on delivering value for that need. The report lays out what STRIDE is and how it is used, what the CIA triad is and why it is important in prioritizing threats, and how the Threat Profile is ultimately developed as quickly and efficiently as possible.
Next Steps and Opportunities to Engage with the SSC at PNNL
With SSC’s efforts, PNNL has demonstrated its commitment to VOLTTRON development and to cybersecurity within the VOLTTRON platform. As more users (including utilities) examine VOLTTRON’s functionality and evaluate its usefulness, the security of the platform becomes more critical. The SSC team seeks your input in four ways:
Providing more use cases. If you have a use case and wish to have a Threat Profile developed, SSC would like to work with you.
Feedback on the current Threat Profile. SSC wants to improve its processes. If you see gaps in the controls, scenarios missing, or a lack of coverage, SSC wants to hear about it. This only makes VOLTTRON better in the end.
Prioritize mitigations. Which aspects have the greatest potential impact for your use case. Help SSC prioritize findings to best reflect real world usage of the platform.
Anything else. If you have other ideas, SSC would like to hear from you.
If you have any interest at all in working with SSC, please reach out to them directly by contacting Chance Younkin (chance.younkin@pnnl.gov) or reach out to me at Andrew@aceiotsolutions.com.


